Students can Download 2nd PUC Computer Science Model Question Paper 1 with Answers, Karnataka 2nd PUC Computer Science Model Question Papers with Answers helps you to revise the complete Karnataka State Board Syllabus and score more marks in your examinations.
Karnataka 2nd PUC Computer Science Model Question Paper 1 with Answers
Time: 3 Hrs. 15 Min.
Max. Marks: 70
PART-A
I. Each question carries one mark. (10 × 1 =10)
Question 1.
What is microprocessor?
Answer:
It is a program controlled semiconductor device (1C), which fetches, decode and executes instructions.
Question 2.
Write the standard symbol for AND gate.
Answer:

Question 3.
What are data structures?
Answer:
A data structure is a systematic way of organising, storing and accessing data.
Question 4.
Is it possible to access data outside a class?
Answer:
Yes, the public members can be accessed by member functions of the class and nonmember function (outside the class) of the class.
Question 5.
How do we initialize a pointer?
Answer:
The initialisation of pointer:
Pointervariable = &variable;
For example;
int a, *ptr;
ptr = &a;
From the above, address of variable ‘a’ is assigned to variable ‘ptr’.
Question 6.
What is normalization?
Answer:
Normalization is the process of reorganizing data in a database by eliminating duplication and ensuring data dependencies.
Question 7.
Expand ARPANET.
Answer:
The Advanced Research Projects Agency Network
Question 8.
What are cookies?
Answer:
A cookie is an HTTP header that consists of text-only data saved on your computer. Cookies are used by Web sites to keep track of their visitors.
![]()
Question 9.
What is the URL?
Answer:
Uniform Resource Locator
Question 10.
Define domain.
Answer:
A domain name is a unique name that identifies a website on the internet.
PART-B
II. Each question carries two marks. (5 × 2=10)
Question 11.
What are the fundamental products for each of the input word
Answer:
ABCD = 0010, ABCD = 0110, ABCD = 1110
Write SOP expression.
ABCD = 0010, ABCD =0110, ABCD = 1110. Write SOP expression.
The SOP expression for ABCD = 0010
\(\overline{\mathrm{A}} \overline{\mathrm{B}} \mathrm{C} \overline{\mathrm{D}}\) = m2
The SOP expression for ABCD =0110,
\(\overline{\mathrm{A}} \mathrm{B} \mathrm{C} \overline{\mathrm{D}}\) = m6
The SOP expression for ABCD = 1110
\(A B C \bar{D}=M_{14}\)
Question 12.
Draw a general K-map for 4-variables A, B, C, and D.
Answer:
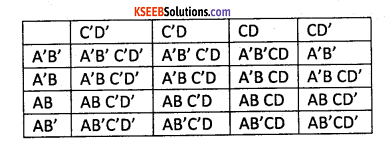
Question 13.
Explain data encapsulation.
Answer:
The data encapsulation is a technique that combines data and functions into a single unit called class. Here, data can be accessed through member function only present inside the class. Data encapsulation enables data hiding or information hiding.
Question 14.
Why are constructors needed in a program? Justify.
Answer:
The objects are not automatically initialized when created. The explicit call to initialization member function can only initialize the object. This method proves to be inconvenient when large number of objects need to be initialized by giving separate function calls. This problem can be overcome by automatically initializing objects when they are created using constructor.
![]()
Question 15.
Differentiate between ifstream class and ofstream class.
Answer:
- The ifstream class supports input operations whereas ofstream class supports output operations on file.
- The ifstream class inherits functions from is tream whereas stream class inherits functions from ostream.
- The inherited member functions of ifstream are get(), getlineQ, read(), seekgQ and tellgO whereas ofstream member function are put(), write(), seekp() and tellp().
Question 16.
What is relational algebra?
Answer:
Relational algebra is a formal system for manipulating relations. Operands of this algebra are relations (a set of tuples). Operations of this algebra include the usual set operations and special operations defined for relations. The Fundamental operations of Relational algebra are Select, Project, Union, Set different, Cartesian product.
Question 17.
What are the logical operators in SQL?
Answer:
The logical operators in SQL are ALL, AND, ANY BETWEEN, EXISTS, IN, LIKE, NOT, OR, IS NULL, UNIQUE.
Question 18.
What is a SIM card?
Answer:
A Subscriber Identity Module (SIM) card is a portable memory chip used mostly in cell phones. These cards hold the personal information of the account holder, including his or her phone number, address book, text messages, and other data.
PART – C
III. Each question carries three marks. (5 × 3 = 15)
Question 19.
Explain the characteristics of motherboard.
Answer:
1. Physical characteristics, which in combination are called the form factor like XT, AT Baby AT and ATX motherboard;
2. The chipset used, which defines the capabilities of the motherboard such as an AMD, Intel, NVidia, SiS, or VIA chipset;
3. The processors the motherboard supports; Different processors use different sockets or slots.
Question 20.
Draw the logic gate diagram to implement NOT gate using NAND and NOR gate.
Answer:
Logic gate diagram to implement NOT gate using NAND

Logic gate diagram to implement NOT gate using NOR

Question 21.
Explain the memory representation of queue using arrays.
Answer:
- Let Q be a linear array of size N
- The pointer FRONT contains location of front element of the queue (element to be deleted)
- The pointer REAR contains location of rear element of the queue (recently added element)
- The queue is empty when FRONT = 0
- The queue is full when REAR = N To add element, REAR = REAR + 1
- To delete element, FRONT = FRONT +1
Question 22.
What is new operator in C++? Give example.
Answer:
The new operator in C++ allocates memory dynamically.
Syntax:
pointervariable = new datatype;
Example:
ptr = new int;
Question 23.
Mention the types of file organisation. Explain anyone.
Answer:
The different types of file organsiation are sequential or serial organization, Direct Access or Random organization, Indexed sequential Access Method (ISAM).
Sequential or serial organization:
In sequential access, records within a file are read or written in sequential order i.e., in the same order they are organized in the file. In sequential or serial access, the information can be retrieved in the same sequence in which it is stored. The data records are arranged one after the other. The records are stored on the basis of order of the record.
In sequential organization, the data records are stored in a predetermined order based on the key fields. There is a definite relationship between logical position and physical position. The key field organizes the records
![]()
Question 24.
Give the different notations for the E-R diagram.
Answer:
The different notations for E-R Diagram
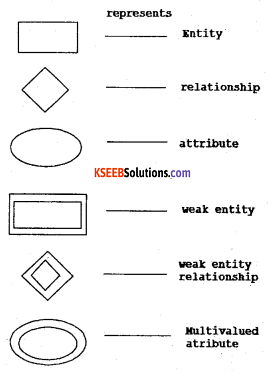
Question 25.
Write the advantages of WWW.
Answer:
Advantages of WWW:
- Availability of mainly free information
- Reduces the costs of information
- The same protocol of communication can be used for all the services
- Provide rapid interactive communication
- Provides the exchange of huge volumes of data
Question 26:
What are the steps involved in hosting a webpage?
Answer:
The steps involved in hosting a webpage are
- Selecting type of web hosting services
- Installation of web applications
- Domain registration
- Developing web content and
- Uploading HTML files
PART-D
IV. Each question carries five marks. (7 × 5 = 35)
Question 27.
State and prove De Morgan’s theorem algebraically.
Answer:
DeMol’gan’s Theorems:
a. (A + B) = A* B
b. A*B = A + B
Proof of DeMorgan’s Theorem (b):
For any theorem X = Y, if we can show that X Y = 0, and that X + Y = 1, then by the complement postulates, A A = 0 and A + A = 1, X = Y. By the uniqueness of the complement, X = Y. Thus the proof consists of showing that (A*B)*( A + B) = 0; and also that (A*B) + ( A + B) = 1.
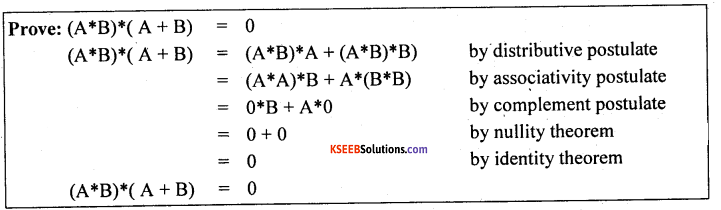
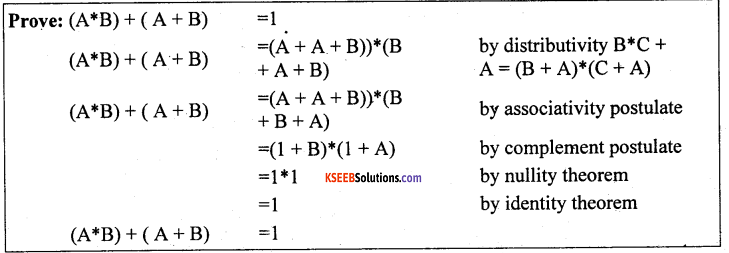
Question 28.
What are the operations performed on linear data structures?
Answer:
The various operations performed on linear data structures are
1. Traversal:
The process of accessing each data item exactly once to perform some operation.
2. Insertion:
The process of adding a new data item into the given collection of data neats.
3. Deletion:
The process of removing existing data item from the given collection of data items.
4. Searching:
The process of finding the location of a data item in the given collection of data items.
5. Sorting:
The process of arrangement of data items in either ascending or descending order.
6. Merging:
The process of combining the data items of two structures to form a single structure.
![]()
Question 29.
Write an algorithm to insert an element into the array.
Answer:
A is an array
N is number of elements (size)
Element is a data element
Pos is location of element to be inserted.
Insertion (A, N, Element, Pos)
Step 1: for i = N-l downto Pos repeat step 2
Step 2: A(i+1] = A[i]
End for
Step 3: A [Pos] = Element
Step 4: N = N + 1
Question 30.
Explain the advantages of OOP.
Answer:
The advantages of OOP are
1. OOP provides a clear modular structure for programs. Large problems can be reduced to smaller and more manageable problems.
2. In OOP, data can be made private to a class such that only member functions of the class can access the data. This principle of data hiding helps the programmer to build a secure program.
3. Implementation details are hidden from other modules and other modules has a clearly defined interface.
4. It is easy to maintain and modify existing code as new objects can be created with small differences to existing ones.
5. With the help of polymorphism, the same function or same operator can be used different purposes. This helps to manage software complexity easily.
6. In OOP, programmer not only defines data types but also deals with operations applied for data structures.
7. It is easy to model a real system as real objects are represented by programming objects in OOP.
8. With the help of inheritance, we can reuse the existing class to derive a new class such that the repetition of code is eliminated and the use of existing class is extended. This saves time and cost of program.
Question 31.
Illustrate with an example of how an array of objects can be defined.
Answer:
The arrays can be used as data members and objects as well. For example,

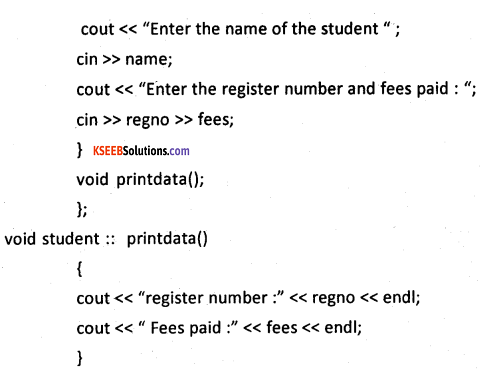

in the above example, data members are name, Regno, and fees are data members. The getdata() and printdataQ are the members functions of the class student and obj is an array of objects of type class student. The for loop is used to pass value to data members. for all the objects and another time for loop is used to print the data values of data members of the class.
Question 32.
Explain the features of copy constructor.
Answer:
The features of copy constructors are
- copy constructor is a special type of parameterized constructor.
- It is normally used to copy one object into another.
- They are normally used to initialize object with values of already existing object.
- Copy constructors should have at least one argument of the same class and must be passed as a constant reference type.
- The copy constructor cannot be invoked explicitly but can be equated to an already existing object in the declaration itself.
For example:
x a1; _ _ _ default constructor invoked
X a2 = a1; _ _ _ copy constructor invoked.
The C++ compiler creates default copy constructor automatically.
![]()
Question 33.
Write a C++ program to find the volume of a cone, cube, and cylinder using overloaded function.
Answer:
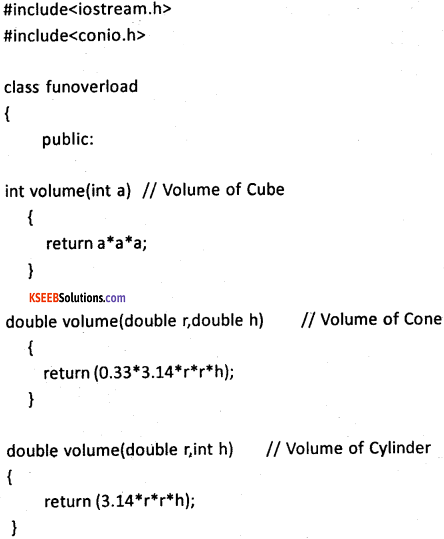

Question 34.
What are the types of inheritance? Explain any two.
Answer:
The different type of inheritances is Single inheritance, Multiple Inheritance, Hierarchical Inheritance, Multi-level inheritance, and Hybrid inheritance.
1. Single inheritance:
A derived class with only one base class is called single inheritance. For example, If A is base class then class 6 derive from base class A.
2. Multilevel inheritance:
A class can be derived from another derived class which is known as multilevel inheritance. For example, The derived class C inherit B class whereas B is derived from class A.
Question 35.
Explain the Codd’s rules for database management.
Answer:
Dr. Edgar Frank Codd was a computer scientist while working for IBM he invented the relational model for database management. Codd proposed thirteen rules (numbered zero to twelve) and said that if a Database Management System meets these rules, it can be called as a Relational Database Management System. These rules are called as Codd’s 12 rules
Rule Zero:
- The system must qualify as relational, as a database, and as a management system.
- The other 12 rules derive from this rule. The rules are as follows :
Rule 1:
The information rule:
All information in the database is to be represented in one and only one way, namely by values in column positions within rows of tables.
Rule 2:
The guaranteed access rule:
All data must be accessible. This rule is essentially a restatement of the fundamental requirement for primary keys. It says that every individual value in the database must be logically addressable by specifying table name, column name and the primary key value of the row.
Rule 3:
Systematic treatment of null values:
The DBMS must allow each field to remain null (or empty). The NULL can be represented as “missing information and inapplicable information” that is systematic, distinct from all regular values, and independent of data type. Such values must be manipulated by the DBMS in a systematic way.
Rule 4:
Active online catalog based on the relational model:
The system must support an online, inline, relational catalog that is accessible to authorized users by means of their regular query language
Rule 5:
The comprehensive data sublanguage rule:
The system must support at least one relational language that
- Has a linear syntax
- Can be used both interactively and within application programs,
- Supports data definition operations, data manipulation operations, security and integrity constraints, and transaction management operations.
Rule 6:
The view updating rule:
All views that can be updated theoretically, must be updated by the system.
Rule 7:
High-level insert, update, and delete:
This rule states that insert, update, and delete operations should be supported for any retrievable set rather than just for a single row in a single table.
Rule 8:
Physical data independence:
Changes to the physical level (how the data is stored, whether in arrays or linked lists etc.) must not require a change to an application based on the structure.
Rule 9:
Logical data independence:
Changes to the logical level (tables, columns, rows, and so on) must not require a change to an application based on the structure.
Rule 10:
Integrity independence:
Integrity constraints must be specified separately from application programs and stored in the catalog. It must be possible to change such constraints as and when appropriate without unnecessarily affecting existing applications.
Rule 11:
Distribution independence:
The distribution of portions of the database to various locations should be invisible to users of the database. Existing applications should continue to operate successfully.
Rule 12:
The non subversion rule:
If the system provides a low-level (record-at-a-time) interface, then that interface cannot be used to subvert the system, for example, bypassing a relational security or integrity constraint
Question 36.
Write the differences between order by and group by commands with example.
Answer:
SQL ORDER BY – clause is used in a SELECT statement to sort results either in ascending or descending order.
The syntax for using SQL ORDER BY clause to sort data is:
> SELECT column-list FROM table_name ORDER BY column1, column2,.. column [DESC]];
For Example: If you want to sort the employee table by salary of the employee, the SQL query would be.
> SELECT name, salary FROM employee ORDER BY salary;
By default, the. ORDER BY Clause sorts data in ascending order. If data to be sorted in descending order, the command would be as given- below
> SELECT name, salary FROM employee ORDER BY name, salary DESC;
SQL GROUP BY Clause –
The SQL GROUP BY Clause is used with the group functions to retrieve data grouped according to one or more columns.
The basic syntax of GROUP BY clause is given below. The GROUP BY clause must follow the conditions in the WHERE clause and must precede the ORDER BY clause if one is used.
> SELECT column1, column2 FROM table_name WHERE [ conditions ]
GROUP BY column1, column2
ORDER BY column1, column2
For Example: If you want to know the total amount of salary spent on each department, the query would be:
> SELECT dept, SUM (salary) FROM employee GROUP BY dept;
The group by clause should contain all the columns in the select list expect those used along with the group functions.
> SELECT location, dept, SUM (salary) FROM employee GROUP BY location, dept;
![]()
Question 37.
Give the measures of preventing virus.
Answer:
The different measures for preventing virus are
1. Always use licensed software.
2. Password protect your PC to prevent unattended modification.
3. Install quality antivirus:
The users should install professional, business-grade antivirus software on their PCs. Pro-grade antivirus programs update more frequently throughout the, protect against a wider range of threats (such as rootkits), and enable additional protective features (such as custom scans).
4. Install real-time anti-spyware protection Use of professional (or fully paid and licensed) anti-spyware programs are required to prevent infections and fully remove those infections already present.
5. Disable autorun:
Many viruses work by attaching themselves to a drive and automatically installing themselves. As a result, connecting any network drives, external hard disks, or even thumb drives to a system can result in the automatic propagation of such threats. The users can disable the Windows autorun feature to avoid.
6. Don’t click on email links or attachments:
Users should never click on email attachments without at. least first scanning them for viruses using a business-class anti-malware application. As for clicking on links, users should access Web sites by opening a browser and manually navigating to the sites.