Students can Download 2nd PUC Computer Science Model Question Paper 2 with Answers, Karnataka 2nd PUC Computer Science Model Question Papers with Answers helps you to revise the complete Karnataka State Board Syllabus and score more marks in your examinations.
Karnataka 2nd PUC Computer Science Model Question Paper 2 with Answers
Time: 3 Hrs. 15 Min.
Max. Marks: 70
PART-A
I. Each question carries one mark. (10 × 1 =10)
Question 1.
What is the function of North Bridge in the motherboard?
Answer:
The northbridge is an integrated circuit (1C ) is responsible for communication between ‘ the CPU interface, AGP, and the RAM memory.
Question 2.
Define logic gate.
Answer:
A gate is an electronic circuit that operates on one or more signals and always produces an output signal.
Question 3.
What are primitive data structures?
Answer:
Data structures that are directly operated upon by machine level instructions are known as primitive data structures.
Question 4.
How are member functions defined?
Answer:
The member function can be defined inside the class definition and outside the class definition.
Question 5.
What is dynamic memory?
Answer:
Allocation of memory at the time of execution (run time) is known as dynamic memory allocation.
Question 6.
What is an attribute?
Answer:
An attribute is the characteristic property of an existing entity.
Question 7.
What do you mean by transmission modes?
Answer:
The way in which data is transmitted from one place to another is called data transmission mode. It des indicates the direction of flow of information.
![]()
Question 8.
What is a SIM card?
Answer:
A Subscriber Identity Module (SIM) card is a portable memory chip used mostly in cell phones. These cards hold the personal information of the account holder, including his or her phone number, address book, text messages, and other data.
Question 9.
Expand IPR.
Answer:
The expansion of IPR is Intellectual Property Rights
Question 10.
What is DHTML?
Answer:
Dynamic HTML is an extension to HTML that will enable a web page to react to user input without sending requests to the web server.
PART-B
II. Each question carries two marks. (5 × 2=10)
Question 11.
Convert the expression (A+C) (C+D) to canonical Product of Sum form.
Answer:

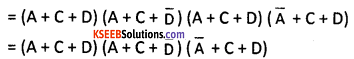
Question 12.
Given the expression in four variables, draw the K-map for the function m2+m3+m5+m7+m9+m11+m13.
Answer:
a) m2+m3+m5+m7+m9+m11+m13.
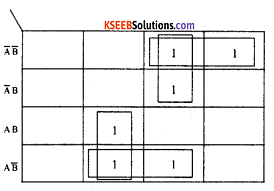
Question 13.
What is the difference between program module and an object?
Answer:
A program module is a self-contained independent program segment only it does not provide security to data whereas an object is a collection of data members and member functions that operate on data and data is provided with security.
Question 14.
Mention the features of parameterized constructors.
Answer:
The features of parameterized constructors are
- parameterized constructors can be overloaded
- parameterized constructors can have default arguments and default values.
![]()
Question 15.
Mention the methods of opening files within C++ program.
Answer:
The methods of opening file within C++ program
- Opening a file using constructor
- Opening a file using member function open()
Question 16.
What is the difference between serial and direct access file organization?
Answer:
In sequential access data is stored at random locations.
- In direct access data is stored at sequential locations.
- Data structure implementing Sequential access is linked list.
- Data structure implementing Direct access is an Array.
Question 17.
Explain the features of SQL.
Answer:
The features of SQL:
- SQL is an ANSI and ISO standard computer language for creating and manipulating databases.
- SQL allows the user to create, update, delete, and retrieve data from a database.
- SQL is very simple and easy to learn.
Question 18.
Name the different types of cables used in transmission.
Answer:
The different types of cables used in transmission are
- Unshielded Twisted Pair Cable (UTP cable)
- Shielded Twisted Pair (STP) cable
- Coaxial Cable
- Fiber Optic Cable
PART C
III. Each question carries three marks. (5 × 3 = 15)
Question 19.
Explain any three types of motherboard.
Answer:
The three types of motherboard are XT motherboard, AT motherboard and ATX motherboard.
1. XT motherboard:
The extended Technology motherboards are old model motherboards. Slot type processors, Low Insertion Force (LIF) sockets, DIMM RAM slots and ISA slots with 12 pin power connectors can be seen.
2. AT motherboard:
Advanced Technology motherboards has Pin Grid Array (PGA) socket, SDRAM slots, 20 pin power connector, PCI slots, and ISA slots. Example: motherboard for Pentium 3 processors.
3. ATX motherboard:
Advanced Technology extended motherboards are comparatively latest boards with MPGA processor sockets, DDR RAM slots, PCI slots, primary and secondary IDE interfaces, SATA connectors, 20 pin and 24 pin ATX power connectors and USB ports.
![]()
Question 20.
Prove the following rules using the proof of perfect induction
a. XY’ + XY = X
b. X+Y = Y+X
Answer:
a. XY’ + XY = X
By proof of perfect induction X = 0, Y =1 XY’ + XY = X
LHS = 0.0 + 0.1±0 + 0 = 0
By proof of perfect induction X = 1, Y = 0 LHS = 1.1+ 1.0= 1 + 0= 1
b. X + Y = Y + X
By proof of perfect induction X = 0, Y = 1 LHS = 0 + 1 = 1 RHS = 1 + 0=1 LHS = RHS
By proof of perfect induction X = 1, Y = 0 LHS = 1 + 0 = 1 RHS = 0 + 1 = 1 LHS = RHS
Question 21.
Write a short note on arithmetic expression.
Answer:
An expression is a combination of operands and operators that after evaluation results in single value. Operands consist of constants and variables. Operators consist of +,-, *, /.. etc., The different methods for evaluation of arithmetic expressions are Infix expression, Postfix expression, and Prefix expression.
1. Infix expression:
If an operator is in between two operands then it is called infix expression. For example A+B
2. Postfix expression:
If an operator follows the two operands, it is called postfix expression. For example, AB +
3. Prefix expression:
If an operator precedes two operands, it is called prefix expression. For example, + AB
Question 22.
How to declare and initialize pointer? Give example.
Answer:
The pointer declaration syntax:
datatype *pointername;
To initialize pointer:
pointervariable = &variable;
For example; inta, *ptr;
ptr = &a; .
From the above, address of variable ‘a’ is assigned to variable ‘ptr’.
Question 23.
Write the different member functions belonging to stream class.
Answer:
The member functions belonging to fstream class are constructor, open, is_open, close, and inherits get(), getline(), read(), seekg() and tellg() from istream, inherits put(), write() seekp() and tellp() from ostream.
Question 24.
Explain any three components of E-R diagram.
Answer:
The three main components of E-R diagram are Entity, Attribute, and Relationship.
1. Entity:
An entity is a person, place, thing or event for which data is collected and maintained.
2. Attribute:
An attribute is the characteristic property of an existing entity.
3. Relation:
A relation is defined as a set of tuples that have the same attributes. A relation is usually described as a table, which is organized into rows and columns.
![]()
Question 25.
Write the advantages of WWW.
Answer:
Advantages of WWW
- Availability of mainly free information
- Reduces the costs of information
- The same protocol of communication can be used for all the services
- Provide rapid interactive communication
- Provides the exchange of huge volumes of data
- Provides access to different sources of information, which is continuously up-dated
PART-D
IV. Each question carries five marks. (7 × 5 = 35)
Question 26.
Use Karnaugh map to reduce the given functions using SOP form. Draw the logic gate diagrams for the reduced SOP expression. You may use gates with more than two inputs. Assume that the variables and their complements are available as inputs.
Answer:
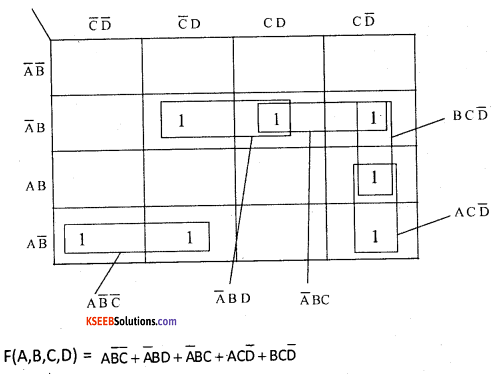
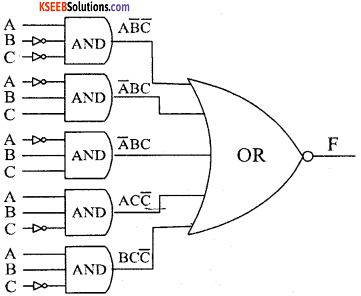
Question 27.
Write a short note on stack.
Answer:
A stack is an ordered collection of items in which data items may be inserted and deleted at one end. This end is referred as “top”. The opposite to top is known as “base”. The most recently added item in the stack is removed first. This working principle is sometimes called LIFO (Last In First Out). Newer inserted elements will be near the top and elements that are inserted at the beginning are near the base.
The applications of stack:
- Arithmetic Expression evaluation
- Arithmetic Expression conversion
- Recursive function .
- Backtracking (game playing, finding paths, exhaustive searching)
- Memory management, run-time environment for nested language features.
The operation on stack is
- stack() creates a new empty stack,
- push(item) insert new item at the top of stack,
- pop() removes the top element from the stack,
- peek() returns the top item of the stack,
- Empty() checks the stack is empty or not and
- size() returns number of items present in the stack
Question 28.
Write an algorithm to delete a data element from the front end of the queue.
Answer:
Step 1: if FRONT = -1 then
Print “Queue is Underflow”
Exit
End of if
Step 2: ITEM = QUEUE [FRONT]
Step 3: if FRONT = REAR then
FRONT = 0 REAR = 0
Else
FRONT = FRONT+1
Step 4: return
Question 29.
Write a short note on inheritance and polymorphism.
Answer:
1. Inheritance:
Inheritance is the process of creating new classes, called derived class, from existing or base classes. The derived class inherits all the capabilities of the base class. Using Inheritance some qualities of the base classes are added to the newly derived class, apart from its own features. Inheritance permits code reusability. The different types of inheritance are single inheritance, multilevel inheritance, multiple inheritance, hierarchical inheritance, and hybrid inheritance.
2. Polymorphism:
The polymorphism is ability of an object to take more than one form in different instances. For example, one function name can be used for different purposes. Similarly, same operator can be used for different operations. There are of two types one is the “compile time polymorphism” and other one is the “run-time polymorphism”. The polymorphism is implemented using function overloading and operator overloading in C++.
Question 30.
Illustrate how an array of objects can be defined.
Answer:
The arrays can be used as data members and objects as well. For example,

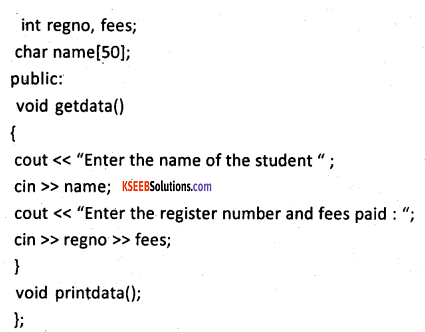
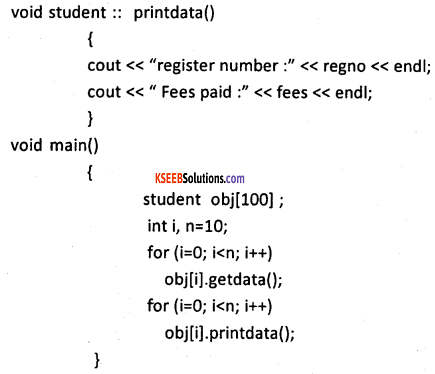
in the above example, data members are name, Regno, and fees are data members. The . getdata() and printdataQ are the members functions of the class student and obj is an array of objects of type class student. The for loop is used to pass value to data member for all the objects and another time for loop is used to print the data values of data. members of the class.
![]()
Question 31.
Write a short note on function overloading.
Answer:
Function overloading means two or more functions having same name but different types of arguments or different numbers of arguments. Function overloading is also known as compile time polymorphism. Function overloading is normally used when several functions of the same name perform identical tasks on different data types.
Reasons for function overloading.
- The overloading function helps to reduce the use of different names for many functions.
- The developer of the program can use one function name to give function call to one in many functions. This reduces selecting a function block to give a function call by the user.
- It is easier to understand the flow of information that helps in faster debug.
- Easy program maintenance.
The restrictions on overloaded functions are
- The parameters/arguments should differ in the number of arguments or if they have same number of argument then they should differ in the type of the arguments
- The use of typedef keyword for naming functions is not treated as different type but is only a synonym for another type.
Declaration and Definition of overloaded functions:
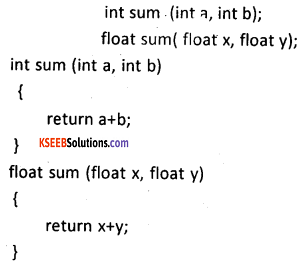
Question 32.
Write a short note on destructors.
Answer:
It is a special function used to release the memory space allocated by the object.
- Name of the Destructor is similar to the class, which it belongs.
- It does not have argument(s) and doesn’t return any value (no return type)
- Destructor is preceded by ~ (tilde) sign.
Following points should be kept in mind while defining and writing the syntax for the destructor: - A destructor function must be declared with the same name as that of the class too. which it belongs.
- The first character of the destructor name must begin with a tilde (~).
- A destructor function is declared with no return types specified (not even void).
- A destructor function must have public access in the class declaration.
General Syntax of Destructors:
~ classname();
The above is the general syntax of a destructor. In the above, the symbol tilde ~ represents a destructor that precedes the name of the class.
![]()
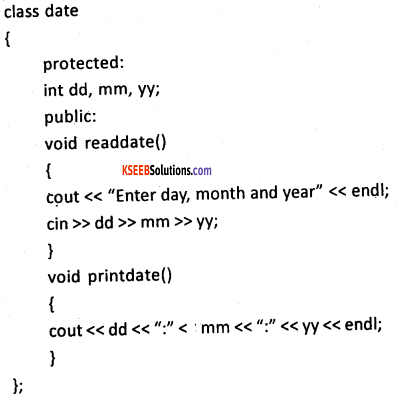
Question 33.
Explain multiple inheritances with a suitable C++ program.
Answer:

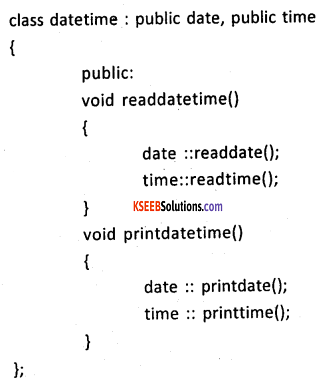
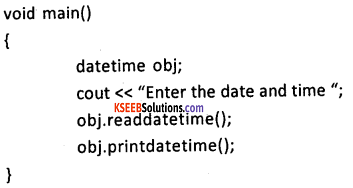
Question 34.
Explain Chen’s style and Martin’s style of relation.
Answer:
Cardinality specifies how many instances of an entity relate to one instance of another, entity i.e., it specifies the occurrences of relationship and also specifies the maximum number of relationships. The cardinality notation can be shown using Information Engineering style, Bachman style, Chen style, and Martin style.
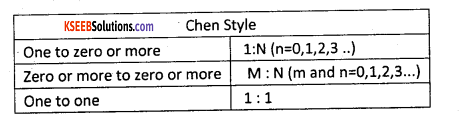
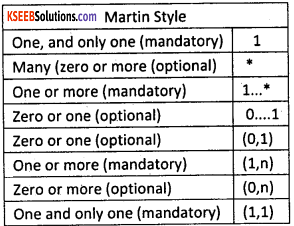
Question 35.
List the built-in functions associated with Group functions in SQL.
Answer:
The built-in functions associated with GROUP functions in SQL are
1. COUNT function:
returns the count of records that satisfies the condition for each group of records.
Example:
SELECT department, COUNT(*)FROM employees WHERE salary > 25000 GROUP BY department;
2. MAX function:
returns the maximum values from the column for each group of records.
Example:
SELECT department, MAX(salary) FROM employees GROUP BY department;
3. MIN function:
returns the lowest values from the column for each group of records.
Example:
SELECT department, MIN(salary)FROM employees GROUP BY department;
4. AVG function:
returns the average values from the column for each group of records. SELECT AVG(cost) FROM products WHERE category = ‘Clothing’;
5. SUM function:
returns the total values from the column for each group of records.
Example:
SELECT department, SUM(sales)FROM order_details GROUP BY department;
DISTINCT function:
returns the once occurrence of many repeated values from the column for each group of records.
SELECT AVG(DISTINCT cost)FROM products WHERE category = ‘Clothing’;
![]()
Question 36.
Explain network security in detail.
Answer:
Network security refers to any activities designed to protect the network and related. activities. It protects the usability, reliability, integrity, and safety of network and data. Good network security identifies variety of threats and stops them from entering or spreading on network.
The network security concerns with allowing only legal or authorized users and programs to gain access to information resources like databases. It also ensures that properly authenticated users get access only to those resources that they are supposed to use.
Many network security threats today are spread over the Internet. The most common include:
- Viruses, worms, and Trojan horses
- Spyware and adware
- Zero-day attacks also called zero-hour attacks
- Hacker attacks
- Denial of service attacks
- Data interception and theft
- Identity theft
A network security system usually consists of many components. Ideally, all components work together, which minimizes maintenance and improves security.
Network security components include:
- Anti-virus and anti-spyware
- Firewall, to block unauthorized access to your network
- Intrusion prevention systems (IPS), to identify fast-spreading threats, such as zero-day or zero-hour attacks
- Virtual Private Networks (VPNs), to provide secure remote access
The network security make use of variety of resources like user name, password, encrypted smart cards, biometrics, and firewalls to protect resources.